How Ray Tracing Hardware Revolutionized Real-Time Graphics

TL;DR: Zero-trust security eliminates implicit network trust by requiring continuous verification of every access request. Organizations are rapidly adopting this architecture to address cloud computing, remote work, and sophisticated threats that rendered perimeter defenses obsolete.
By 2027, security analysts predict that 60% of enterprise organizations will phase out traditional VPNs in favor of zero-trust network access. What began as a theoretical framework is now the dominant security paradigm, fundamentally reshaping how we protect digital assets. This transformation is driven by harsh lessons: the average data breach now costs $4.45 million, and 83% of organizations have experienced more than one breach. Traditional perimeter defenses, designed for an era when employees worked inside office buildings and applications ran in data centers, have collapsed under the weight of cloud computing, remote work, and increasingly sophisticated attackers who exploit the simple assumption that once you're inside the network, you're trusted.

For decades, enterprise security operated on a castle-and-moat model. Build strong walls, authenticate users at the gate, and trust everything inside. This worked reasonably well when corporate networks had clear boundaries and employees sat at desks connected to local area networks. Once authenticated through a VPN, users could access virtually any internal resource.
That world no longer exists. Cloud services scattered corporate data across AWS, Azure, and Google Cloud. Remote work became permanent. Mobile devices multiplied access points. APIs connected applications across organizational boundaries. The old perimeter dissolved, yet many organizations continued securing networks as though boundaries still mattered. Attackers noticed. They exploited this trust model relentlessly, moving laterally through networks once they gained initial access.
Traditional perimeter security failed for several technical reasons. First, it assumed network location indicated trust level—inside the network meant trustworthy, outside meant suspicious. This assumption proved catastrophically wrong when attackers compromised insider credentials or when malicious insiders existed. Second, it granted excessive permissions. Once authenticated, users could typically access far more resources than their job required. Third, it provided limited visibility into what happened after authentication, creating blind spots where threats moved undetected.
The old security perimeter has dissolved. Cloud computing, remote work, and mobile devices have made network boundaries meaningless, yet many organizations still defend them as though they matter.
The failures weren't hypothetical. Misconfigured cloud resources exposed 2.2 billion records in 2021 alone. Ransomware operators routinely used legitimate credentials to access networks, then moved laterally for weeks before deploying encryption. The 2020 SolarWinds breach compromised multiple government agencies and corporations because attackers leveraged trusted network access to install backdoors. Each incident reinforced the same lesson: implicit trust, regardless of source, creates vulnerability.
Zero-trust security operates on a radically different premise: trust nothing by default, verify everything continuously. Every user, device, application, and network flow must prove its identity and authorization before accessing resources—not just once at login, but throughout the entire session. Location means nothing. Being inside the corporate network confers no special privileges. The mantra is simple: "never trust, always verify."
This philosophy emerged from research at Forrester Research in 2010, when analyst John Kindervag coined the term "zero trust" to describe security architectures that eliminated implicit trust. Google pioneered practical implementation with BeyondCorp, its internal zero-trust system launched in 2011 after experiencing sophisticated attacks. The U.S. government accelerated adoption dramatically when President Biden's 2021 Executive Order 14028 mandated federal agencies implement zero-trust architecture, treating it as critical national security infrastructure.

The National Institute of Standards and Technology (NIST) codified zero-trust principles in Special Publication 800-207, establishing the architectural standard. NIST defined three core tenets that underpin all zero-trust implementations:
Verify explicitly: Authenticate and authorize based on all available data points—user identity, location, device health, service or workload, data classification, and anomalies. Never assume credentials alone suffice.
Least privilege access: Limit user access with Just-In-Time and Just-Enough-Access (JIT/JEA), risk-based adaptive policies, and data protection. Users receive the minimum permissions necessary for their current task, and nothing more.
Assume breach: Minimize blast radius for breaches and prevent lateral movement. Verify end-to-end encryption. Use analytics to gain visibility, detect threats, and improve defenses. Operate as though attackers are already inside the network, because they probably are.
These principles transform security from perimeter defense to identity-centric protection. The focus shifts from "where are you connecting from?" to "who are you, what device are you using, what do you need access to right now, and does your behavior match normal patterns?"
Implementing zero-trust requires orchestrating multiple security technologies into a cohesive system. Organizations must verify identities continuously, assess device security posture, segment networks microscopically, and monitor behavior constantly. Each component reinforces the others, creating defense in depth without trusting any single layer.
Identity becomes the new perimeter. Zero-trust architectures treat every authentication request as potentially hostile, requiring multi-factor authentication (MFA) at minimum, ideally using phishing-resistant methods like hardware security keys or biometrics. But authentication doesn't end after initial login.
Continuous authentication monitors user behavior throughout sessions, analyzing factors like typing patterns, mouse movements, access times, and resource requests to detect anomalies. If a user who normally accesses customer databases from Chicago suddenly requests payroll data from Romania, the system challenges the request—reauthenticating or blocking access automatically. This happens transparently, without disrupting legitimate users.
"Zero-trust isn't about blocking access—it's about verifying continuously that the right people access the right resources at the right times, with minimal friction for legitimate users."
— Security Architecture Best Practices
Modern identity platforms integrate with hundreds of applications, enforcing consistent authentication policies across cloud services, on-premises systems, and mobile apps. Identity has become the cornerstone of zero-trust implementations because in distributed environments, you can't rely on network position—only on verified identity.

Who's accessing resources matters, but so does what they're accessing from. Zero-trust systems continuously assess device security posture, checking whether devices have current patches, active antivirus, encrypted storage, and compliant configurations. Unmanaged or compromised devices get restricted or denied access entirely.
This device trust verification happens before granting access and continues during sessions. If a device's security posture degrades—antivirus disabled, suspicious processes detected, outdated software found—the system can immediately revoke or limit access. Organizations often segment access based on device trust levels: fully managed corporate devices get broader access than personal bring-your-own-device systems, which may be restricted to web applications only.
Cloud-based device management platforms make this practical at scale, continuously monitoring thousands of devices without requiring complex on-premises infrastructure. Employees access resources through secure gateways that verify both identity and device health before establishing connections.
Traditional networks operated like open office plans—once inside, you could see and access almost everything. Zero-trust networks implement microsegmentation, dividing infrastructure into small, isolated zones where access is explicitly granted per resource, not broadly permitted across network segments.
This architecture dramatically limits lateral movement. When attackers compromise one system, they can't automatically access others. Each connection attempt triggers new verification checks. Microsegmentation creates security boundaries around individual workloads, applications, or even data sets, effectively containing breaches.
Zero Trust Network Access (ZTNA) replaces VPNs with more granular controls. Unlike VPNs that grant broad network access once authenticated, ZTNA creates encrypted connections directly between users and specific applications, with continuous verification. Users never gain visibility into the broader network, eliminating reconnaissance opportunities for attackers. Organizations like Microsoft reported that ZTNA implementations reduced security incidents while improving remote access experience.
Zero-trust systems use sophisticated policy engines that make real-time access decisions based on dozens of signals. These engines apply least-privilege access principles dynamically, adjusting permissions based on context: time of day, location, device health, user behavior patterns, data sensitivity, and threat intelligence.
The relationship between zero-trust and least privilege is symbiotic—zero-trust provides the architecture for continuously verifying trust, while least privilege ensures verified users only access what they absolutely need. Policies can automatically elevate privileges temporarily for specific tasks, then revoke them afterward, implementing just-in-time access that minimizes standing privileges attackers could exploit.
Modern zero-trust systems make thousands of access decisions per minute, considering identity, device health, location, behavior patterns, and threat intelligence—all happening transparently behind the scenes.
Zero-trust adoption has accelerated dramatically. By 2024, 78% of organizations had initiated zero-trust deployments, up from just 16% in 2019. This surge reflects converging pressures: expanding attack surfaces, regulatory mandates, remote work permanence, and quantifiable security improvements.
Government mandates accelerated adoption significantly. The Biden administration's Executive Order 14028 required all federal agencies to implement zero-trust architecture, setting aggressive deadlines and detailed requirements. The Cybersecurity and Infrastructure Security Agency (CISA) published a Zero Trust Maturity Model providing implementation roadmaps that agencies—and subsequently private organizations—adopted.

Financial services, healthcare, and critical infrastructure sectors face increasing regulatory pressure to implement zero-trust principles. Compliance frameworks now explicitly reference zero-trust controls, making implementation not just security best practice but regulatory necessity.
Organizations implementing zero-trust report substantial security improvements. Microsoft's zero-trust deployment reduced security incidents by 40% while improving user experience. A Forrester study found Microsoft's zero-trust solutions delivered 92% return on investment over three years, primarily through reduced breach costs and operational efficiencies.
Zero-trust implementations significantly lower breach costs compared to traditional security approaches. Organizations with mature zero-trust architectures identified and contained breaches 90 days faster than those relying on perimeter defenses, directly reducing damage. The math is compelling: if the average breach costs $4.45 million and zero-trust reduces breach likelihood by 40% while cutting containment time in half, ROI becomes obvious.
Operational benefits extend beyond security. Zero-trust simplifies infrastructure because organizations no longer maintain complex VPN concentrators, network segmentation hardware, and perimeter defenses. Cloud-based zero-trust services reduce capital expenditure while providing better scalability than legacy systems.
Despite clear benefits, zero-trust implementation remains complex and gradual. Organizations face technical, cultural, and organizational challenges that make deployment a multi-year journey rather than a simple migration.
Most organizations operate hybrid environments mixing modern cloud services with decades-old legacy systems. Zero-trust architectures integrate smoothly with cloud-native applications using modern authentication protocols, but legacy systems often lack the APIs, logging capabilities, or authentication mechanisms zero-trust requires.
Mainframes, industrial control systems, and specialized business applications built before cloud computing existed present particular challenges. Organizations can't simply replace these systems, so they must implement proxy architectures, protocol translation layers, or isolated security zones that approximate zero-trust principles without full integration.
Zero-trust is complex. It requires coordinating identity management, device security, network microsegmentation, policy engines, and continuous monitoring across diverse environments. Organizations need expertise spanning network engineering, identity management, security operations, and application architecture—skillsets rarely found in single teams.
Implementations demand significant upfront effort. Organizations must inventory all resources, classify data, map application dependencies, define access policies for thousands of combinations, and test extensively before production deployment. Projects commonly span two to four years for large enterprises.
Zero-trust changes how employees work. Frequent authentication challenges, device compliance requirements, and access restrictions feel like friction to users accustomed to VPN-once-then-access-everything workflows. IT teams worry about help desk tickets. Executives worry about productivity impacts.
"The biggest barrier to zero-trust isn't technical—it's cultural. Organizations must balance security with user experience, or employees will find workarounds that undermine the entire architecture."
— Enterprise Security Implementation Study
Successful implementations address these concerns through gradual rollout, user education, and thoughtful design. Modern zero-trust systems can maintain security without degrading user experience by using single sign-on, passwordless authentication, and risk-based policies that challenge users only when behavior seems anomalous. Google's BeyondCorp implementation, for example, actually improved user experience by eliminating VPN bottlenecks while enhancing security.

No single vendor provides complete zero-trust architecture; organizations assemble capabilities from multiple sources. The vendor landscape includes identity specialists, network security platforms, endpoint protection providers, and integrated suites offering partial solutions.
Major cloud providers integrated zero-trust capabilities into their ecosystems. Microsoft's suite includes Azure AD for identity, Intune for device management, and Defender for security monitoring. Google offers BeyondCorp Enterprise for identity-aware access. These platforms work best for organizations heavily invested in their respective clouds but can integrate with multi-cloud environments.
Dedicated zero-trust vendors focus on specific capabilities. Zscaler pioneered cloud-based ZTNA and secure web gateways. CrowdStrike specializes in endpoint protection integrated with zero-trust access controls. Palo Alto Networks offers network security with microsegmentation. Fortinet earned recognition from Gartner as a leader in ZTNA solutions.
Organizations typically use five to ten products from different vendors, integrating them through security information and event management (SIEM) platforms that aggregate logs and coordinate responses. The best implementations focus on interoperability, ensuring identity providers, network security tools, and monitoring systems share threat intelligence and policy decisions.
Google's BeyondCorp remains the canonical zero-trust success story. After experiencing sophisticated attacks in 2009, Google rebuilt its security architecture entirely around zero-trust principles. By 2017, all 85,000 employees accessed applications without VPNs, using device certificates and identity verification instead. Google reported improved security, better user experience, and simplified infrastructure management.
Microsoft's internal zero-trust implementation protected 180,000 employees across 600 locations. The company phased out VPNs entirely, implementing conditional access policies that continuously verify identity and device health. Microsoft reported 40% fewer security incidents, faster breach containment, and reduced IT complexity.
State and local government agencies have adopted zero-trust to protect sensitive citizen data while supporting remote work. Continuous authentication systems allow agencies to maintain security without constant password prompts that frustrated users. These implementations demonstrate zero-trust viability even in resource-constrained environments with diverse legacy systems.
Zero-trust isn't one-size-fits-all; implementation approaches depend on organizational size, existing infrastructure, cloud maturity, and risk tolerance. However, certain strategies increase success likelihood across contexts.
Most successful implementations begin with identity infrastructure. Establish strong identity and access management (IAM) as the foundation, implementing multi-factor authentication, single sign-on, and conditional access policies. This provides immediate security improvement while establishing the control plane for broader zero-trust capabilities.
Modern IAM platforms integrate with thousands of applications, allowing organizations to enforce consistent authentication policies across their environment before tackling network microsegmentation or device compliance.
Successful organizations implement zero-trust incrementally, starting with high-risk applications or crown jewel data. Apply zero-trust principles to the most valuable or exposed resources first, learn from the implementation, refine policies, and gradually expand scope.
Phased approaches allow organizations to demonstrate value, build expertise, and adjust policies based on real usage patterns before enterprise-wide rollout. CISA's Zero Trust Maturity Model provides implementation stages from initial/traditional through optimal/advanced, helping organizations measure progress systematically.
Define key performance indicators (KPIs) for zero-trust success: time to detect threats, lateral movement prevention rates, user authentication friction, policy violation frequency, and incident response times. Measure these metrics consistently, using data to refine policies and identify gaps.
Zero-trust implementation is continuous improvement, not a one-time project. Threat landscapes evolve, organizations change, new applications launch. Policies must adapt. Organizations achieving microsegmentation ROI through reduced breach costs continuously monitor KPIs to justify investment and identify optimization opportunities.
Zero-trust represents more than a technology shift; it's a philosophical transformation in how we approach security. The implications extend far beyond replacing VPNs with ZTNA.
First, zero-trust acknowledges reality: perimeters don't exist anymore, and trust is always conditional. This honesty creates more resilient security because assumptions align with actual threat environments. Organizations stop pretending network boundaries provide meaningful protection and instead focus on continuous verification at the point of access.
Second, zero-trust enables distributed work at scale. Remote employees, contractor access, partner integrations, and multi-cloud operations all become more secure and manageable under zero-trust models than traditional perimeter approaches could ever provide. This flexibility is critical as work continues fragmenting across locations, devices, and organizational boundaries.
Third, zero-trust makes security more measurable and adaptive. By continuously collecting telemetry about access requests, device health, and user behavior, zero-trust systems generate rich data for security analytics. Machine learning models can detect anomalies humans would miss, automating threat response at speeds attackers can't match.
Within five years, organizations without zero-trust will be the exception, not the rule. The question isn't whether to adopt zero-trust, but how quickly you can implement it before the next breach forces your hand.
The transition isn't complete. Many organizations remain in early implementation stages, struggling with legacy systems and cultural resistance. But the direction is irreversible. As research on zero-trust advances, frameworks mature, and automation improves, zero-trust will become the default security model, not an aspirational architecture.
Within five years, explaining why an organization doesn't use zero-trust will require justification, while today, implementing it still does. The castle walls have crumbled. We're learning to thrive in the open field, verifying everything, trusting nothing, and building security that matches the distributed, interconnected reality of modern computing. The transformation is challenging, complex, and absolutely necessary. Organizations that master zero-trust principles now position themselves to adapt as technology evolves, threats intensify, and work becomes even more distributed than today. Those clinging to perimeter defenses won't just fall behind—they'll be breached, repeatedly, expensively, inevitably.
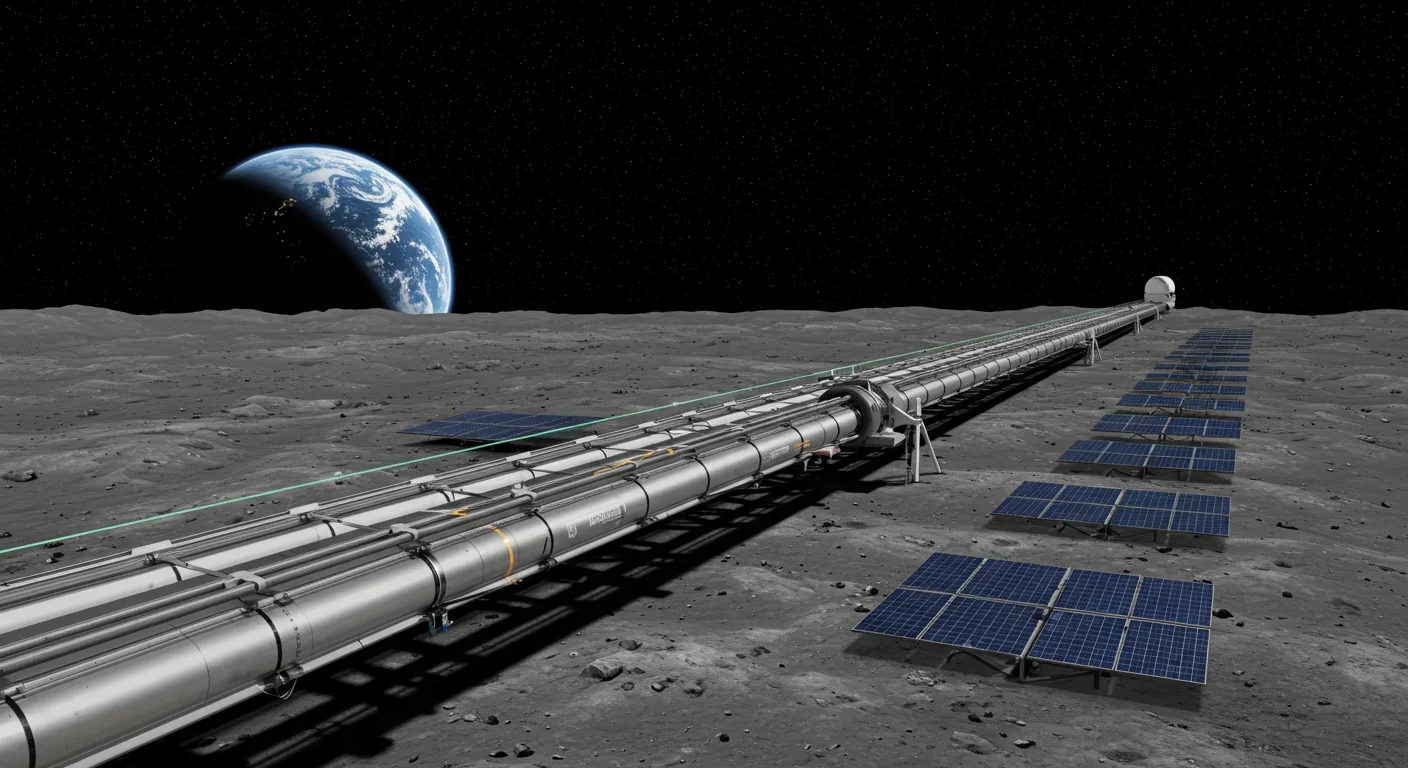
Lunar mass drivers—electromagnetic catapults that launch cargo from the Moon without fuel—could slash space transportation costs from thousands to under $100 per kilogram. This technology would enable affordable space construction, fuel depots, and deep space missions using lunar materials, potentially operational by the 2040s.

Ancient microorganisms called archaea inhabit your gut and perform unique metabolic functions that bacteria cannot, including methane production that enhances nutrient extraction. These primordial partners may influence longevity and offer new therapeutic targets.

CAES stores excess renewable energy by compressing air in underground caverns, then releases it through turbines during peak demand. New advanced adiabatic systems achieve 70%+ efficiency, making this decades-old technology suddenly competitive for long-duration grid storage.

Human children evolved to be raised by multiple caregivers—grandparents, siblings, and community members—not just two parents. Research shows alloparenting reduces parental burnout, improves child development, and is the biological norm across cultures.

Soft corals have weaponized their symbiotic algae to produce potent chemical defenses, creating compounds with revolutionary pharmaceutical potential while reshaping our understanding of marine ecosystems facing climate change.

Generation Z is the first cohort to come of age amid a polycrisis - interconnected global failures spanning climate, economy, democracy, and health. This cascading reality is fundamentally reshaping how young people think, plan their lives, and organize for change.

Zero-trust security eliminates implicit network trust by requiring continuous verification of every access request. Organizations are rapidly adopting this architecture to address cloud computing, remote work, and sophisticated threats that rendered perimeter defenses obsolete.